In March, a software program bug threatened to derail giant swaths of the net. XZ utils, an open-source compression device embedded in myriad software program merchandise and working techniques, was discovered to have been implanted with a backdoor.
The backdoor—a surreptitious entry level into the software program—would have allowed an individual with the requisite code to hijack the machines working it and challenge instructions as an administrator. Had the backdoor been extensively distributed, it might have been a possible catastrophe for tens of millions of individuals.
Fortunately, earlier than the malicious replace may very well be pushed out into wider circulation, a software program engineer from Microsoft seen irregularities within the code and reported it. The venture was subsequently commandeered by accountable events and has since been fastened.
Whereas catastrophe was narrowly averted, the episode has highlighted the continuing liabilities within the open-source improvement mannequin which can be longstanding and never simply fastened. The XZ episode is way from the primary time an open-source bug has threatened to derail giant swaths of the net. It actually gained’t be the final. Understanding the vexing cybersecurity dilemmas posed by open-source software program requires a tour by way of its byzantine and never altogether intuitive ecosystem. Right here, for the uninitiated, is our try to provide you that tour.
The Net Runs on FOSS
At the moment, the overwhelming majority of codebases depend on open-source code. It’s estimated that 70 to 90 % of all software program “stacks” are composed of it. In all probability, the overwhelming majority of the apps in your cellphone have been designed with it, and, if you’re one of many 2.5 billion individuals on the planet who makes use of an Android, your machine’s working system is a modified model of the software program that originated with the Linux kernel—the most important open supply venture on the planet.
When individuals speak about software program “provide chains”—the digital scaffolding that helps our favourite net services and products—a lot of that code is fabricated from open-source parts. Its ubiquity has led observers to consult with open supply because the “essential infrastructure” of the web—a Protean substance that’s each indispensable and extremely highly effective.
But, as essential as it’s, open-source software program stays a topic that isn’t extensively understood by most individuals exterior of the tech business. Most individuals have by no means even heard of it.
Why Use Open Supply?
For the uninitiated, a fast clarification would possibly go one thing like this: In contrast to “closed” or proprietary software program, free and open supply software program, or FOSS, is publicly inspectable and can be utilized or modified by anybody. Its utilization is decided by a wide range of licensing agreements and, fairly uniquely, the parts are sometimes maintained by volunteers—unpaid builders who spend their free time protecting the software program updated and in good working situation.
Open-source tasks can begin as just about something. Typically, they’re small tasks for digital tinkerers who merely wish to construct one thing new. Ultimately, some tasks get well-liked, and personal firms will start incorporating them into their industrial codebases. In lots of instances, when a company improvement crew decides to create a brand new software, they are going to assemble it utilizing a wealth of smaller, already present software program parts that are comprised of a whole lot and even hundreds of traces of code. Lately, most of these parts come from the open-source group.
It may be type of troublesome to image how this odd relationship between industrial software program and the open supply ecosystem works. Fortunately, a number of years in the past the webcomic artist Randall Munroe created what’s now a widely known meme that helps visualize this counterintuitive dynamic:
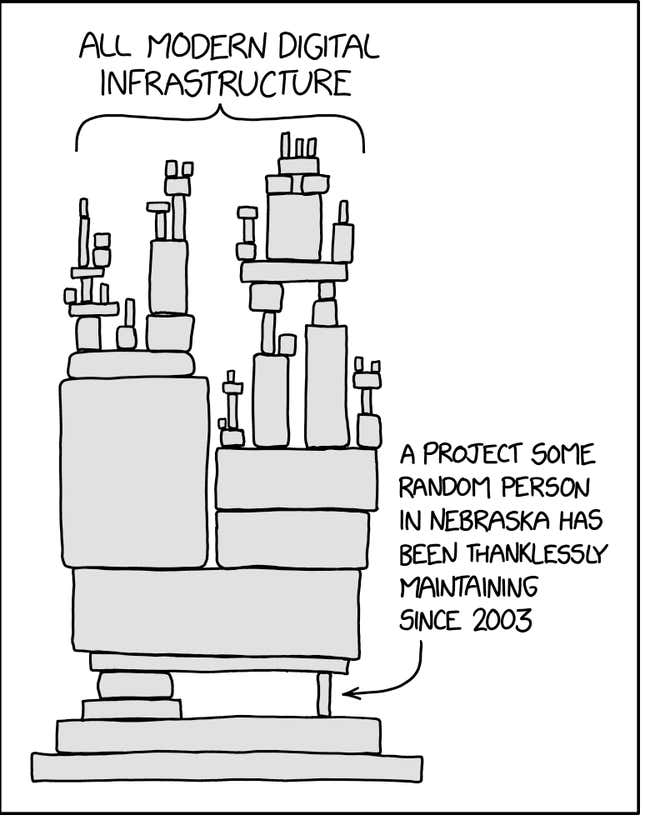
There are lots of causes that firms flip to open supply for his or her improvement wants. Apart from the truth that it’s free, FOSS additionally permits for software program to be created with effectivity and pace. If a programmer doesn’t have to fret concerning the basic constructing blocks of an software’s code, it frees them as much as concentrate on the software program’s extra marketable components. In a aggressive setting like Silicon Valley—the place a speedy time to market is a essential benefit—open supply is just about a DevOps crucial.
However with pace and agility comes vulnerability. If FOSS is a ubiquitous ingredient of contemporary software program, there are additionally structural issues with the ecosystem that put large quantities of software program in danger. These issues can get fairly bushy fairly rapidly—usually with disastrous outcomes.
Bugs From Hell
The XZ episode didn’t finish in catastrophe, but it surely simply might have. One occasion the place net customers weren’t so fortunate was the infamous “log4shell” incident. Three years in the past, in November 0f 2021, a code vulnerability was found within the then-popular open-source program log4j. A logging library, applications like log4j are commonly built-in into apps, the place coders use them to file and assess a program’s inside processes. Log4j, which is maintained by the open-source group Apache, was extensively used on the time of the bug’s discovery and was embedded in tens of millions of purposes all around the world.
Sadly, log4j’s bug—dubbed “log4shell”—was fairly dangerous. Just like the XZ bug, it concerned distant code execution. This meant {that a} hacker might fairly simply inject their very own “arbitrary” code into an impacted program, enabling them to hijack the machine working it. Because of log4j’s reputation, the scope of the bug was large. Main, multi-billion greenback firms have been affected. A whole lot of tens of millions of gadgets have been weak. Within the days after the flaw’s disclosure, consultants estimated that the vulnerabilities have been a ticking time bomb and that cybercriminals have been already seeking to exploit them.
The invention of the bug despatched company America right into a full-blown panic and spooked the best ranges of the federal authorities. Among the largest firms on the planet have been in danger—making it a matter of nationwide safety. A number of weeks after the bug’s discovery, Anne Neuberger, a prime cybersecurity advisor to President Joe Biden, known as a White Home summit on open supply safety, inviting executives from Microsoft, Meta, Google, Amazon, IBM, and different massive names, in addition to influential open supply organizations like Apache, the Linux Basis, and Linux’s Open Supply Safety Basis, or OSSF. The assembly was much less involved with find out how to treatment the hellish vulnerability than with determining find out how to cease this type of factor from ever occurring once more.
Not lengthy after the assembly, prime executives on the Linux Basis, together with then-general supervisor of OSSF Brian Behlendorf, started formulating a so-called “mobilization plan” to higher safe your complete FOSS ecosystem. The federal authorities, in the meantime, started creating its personal methods to additional regulate the tech business. Most notably, President Biden’s cybersecurity plan, which was printed final yr, has sought to prioritize quite a few new safeguards to forestall the emergence of latest, extremely damaging bugs.
But as the hazards surrounding the XZ vulnerability present, FOSS continues to be an setting that, at its highest ranges, is weak to bugs that would have catastrophic, system-wide implications for the web. Understanding the dangers in FOSS, nonetheless, isn’t straightforward. It requires a detour into the distinctive ecosystem that produces a lot of the world’s software program.
Closed Supply Doesn’t Imply Extra Safe
Earlier than we go any additional, it’d be useful to make one factor clear: Simply because a software program program is “closed supply” or proprietary doesn’t imply it’s safer. Certainly, safety consultants and FOSS proponents contend that the other is true. We’ll revisit this challenge once more later however, in the intervening time, I’ll simply direct your consideration to a bit of firm known as Microsoft. This firm, regardless of being a outstanding, closed-source company big, has had its product base hacked numerous instances—generally to disastrous impact. Many firms that preserve their merchandise closed have comparable monitor information, and, not like with open-source software program, their safety points are sometimes stored secret, since no one however the firm has entry to the code.
The Maintainers
If you wish to discuss concerning the safety dangers in open-source software program, it’s a must to begin by speaking concerning the individuals behind the code. Within the open-source ecosystem, these persons are often known as “maintainers” and, as you would possibly anticipate, they’re answerable for sustaining the standard of the software program.
Explaining the function of the maintainer is a bit of sophisticated. Maintainers would possibly aptly be in comparison with the development staff who—in the true world—construct our roads and bridges. Or, the engineers who design them. Or each. Briefly, a maintainer is the caretaker (and infrequently the creator) of a specific open-source venture however, in lots of instances, they work along with “contributors”—customers of the software program who wish to make enhancements to the code.
Maintainers host their open-source tasks on public repositories, the hottest of which is Github. These repositories embrace interactive mechanisms which can be finally managed by the maintainer. For example, when a contributor needs so as to add one thing to a venture, they may submit a “pull request” on GitHub, which incorporates the brand new code they hope so as to add. The maintainer is then tasked with signing off on a “merge,” which can replace the venture to mirror the contributor’s modifications. It’s by way of this collaborative course of that open-source tasks regularly develop and remodel.
Because the grasp controller of those dwelling, iterative tasks, the maintainer’s job usually requires an immense quantity of labor—every little thing from ongoing correspondence with customers and contributors, to signing off on code commits, to creating “documentation” guides that present how every little thing contained in the software program really works. But, for all of that work, a complete lot of maintainers should not paid notably effectively. Most should not paid in any respect. Open supply is meant to be free, keep in mind? On the earth of FOSS, exhausting work is repaid with little greater than the data that your code is being put to good use.
The plight of the maintainer is a peculiar one and may be very a lot tied up with open supply’s sophisticated historical past, in addition to its not altogether simple relationship with the companies that use its code.
A Flash Historical past of FOSS
It’s useful to think about that, to start with, open supply didn’t have a lot to do with corporatism or cash. Actually, it was simply the other.
FOSS grew out of an idealistic hacker motion from the Eighties known as the “free software program” motion. For all intents and functions, that motion started with Richard Stallman—an eccentric laptop scientist who seems to be a bit of like Jerry Garcia and has lengthy espoused a daring type of cybernetic idealism. In 1983, whereas working on the MIT Synthetic Intelligence Lab, Stallman established GNU, a repository of free software program. The thought behind the gathering was person management. Stallman balked at the concept non-public firms might preserve software program behind a walled backyard. He felt that software program customers wanted the power to regulate the applications they used—to see how they labored, in addition to to vary or modify them in the event that they wished. As such, Stallman postulated the concept of “free” software program—famously commenting that he meant free “like free speech, not like free beer.” That’s to say, Stallman shouldn’t be in opposition to builders getting paid, however their code ought to be open and visual to all for future enchancment.
In 1991, a then-21-year-old Finnish laptop programming pupil named Linus Torvalds spurred the subsequent nice innovation in open-source historical past. Reportedly out of boredom, Torvalds created a brand new working system and named it after himself, calling it “Linux.” Pivotally, Torvalds created the Linux “kernel,” the very important element inside any working system that governs the interface between a pc’s {hardware} and its digital processes. It wasn’t clear on the time, however Linux would go on to turn out to be the most important, most well-liked open-source venture on the planet. At the moment, there are a whole lot of Linux distributions (or “distros”) that use the kernel that Torvalds created.
In 1998, a small however influential group contained in the free software program group determined they wished to interrupt away from the motion’s idealistic roots and take the software program mainstream. A summit was held in Mountain View, Calif., the place contributors sought to debate find out how to “re-brand” free software program into one thing “the company world would hasten to purchase,” writes Eric Raymond, a widely known programmer, and one of many assembly’s attendees. “Open supply” was pitched as a “advertising and marketing time period,” invented with the aim of capturing the imaginations of America’s tech titans and steering them away from the vaguer, extra Communist-adjacent terminology of “free,” Raymond explains. The hope was that businessmen would neglect Stallman’s hippy-dippy stuff and purchase into the extra pragmatic-sounding time period.
It seems that they did purchase it. It was the Dot Com bubble, Silicon Valley was booming, and personal enterprise was hungry for brand spanking new methods to unleash income. To many companies, open supply—which offered a shared pool of free labor and an industrial mannequin for innovation—appeared like a good suggestion. The “open supply” motion thus largely splintered from the “free” motion, turning into its personal, corporately-propelled organism, which, in time, took over a higher and higher house contained in the software program business. Linux turned ubiquitous, Torvalds turned well-known, and Stallman largely continued to do what he’d at all times accomplished: advocate for his digital freedoms and disparage the company software program giants. At the moment, the world runs on “open supply,” although it’s nonetheless a time period Stallman categorically rejects. He nonetheless prefers the time period “free” software program.
Code for Nothing
Open-source software program has turn out to be a ubiquitous useful resource for companies, however the builders who’re liable for creating and sustaining that very important materials haven’t at all times seen the help—monetary or in any other case—that they deserve. Certainly, many firms are sometimes content material to seize the code and scat, primarily exploiting the free work with out giving again to the tasks or their creators.
For the previous couple of years, the corporate Tidelift has printed a survey primarily based on interviews with a whole lot of open-source maintainers. Every year, the survey exhibits just about the identical factor: Maintainers are overworked, underappreciated, and burned out. Greater than half of open supply maintainers should not paid in any respect for his or her work, the survey outcomes have proven. A 2020 Linux Basis survey of contributors equally discovered that greater than half of respondents—or roughly 51.65 %—stated they have been unpaid.
Maintainer burnout has been blamed for the XZ incident. Certainly, the unique maintainer of the software program venture reported feeling “behind” on it and finally ceded duty to a person named “Jia Tan.” This person ended up being the one who launched the backdoor into the software program element.
There have lengthy been requires the non-public sector to do extra to help the FOSS ecosystem however, for essentially the most half, these calls have fallen on deaf ears. It’s true that, in recent times, giant tech firms have poured cash into sure sectors of the open-source ecosystem—however usually solely in locations the place it’s advantageous for them to take action.
For the overwhelming majority of FOSS coders, sustaining tasks nonetheless comes with little to no compensation, and it’s usually much less of a enjoyable interest or an actual job than a thankless hustle—suppose the creator economic system with code. On Reddit, you could find thread after thread the place builders focus on methods to bootstrap FOSS financing. Some recommend turning to Liberapay, an open-source crowdfunding platform recognized for doling out cash to cash-stressed devs. Others suppose Patreon is a great possibility. No less than one individual encourages individuals to succeed in out to Gitcoin, a Web3 startup that makes use of cryptocurrency grants to sponsor FOSS tasks. Numerous builders simply incorporate donation portals on their Github venture pages—with hyperlinks to stuff like Stripe, PayPal, or Purchase Me a Espresso. As with most inventive endeavors, begging for cash finally ends up being the surest strategy to make a buck.
Heartbleed
You may most likely think about the safety points that may come up from having an immensely well-liked piece of software program maintained through OnlyFans-type contributions. Research have proven that the overwhelming majority of economic apps comprise open-source parts which can be now not up to date or have been deserted by their maintainers.
The risks inherent in constructing enterprise digital infrastructure off the backs of a decentralized, generally flighty labor pool are readily obvious if the story of Heartbleed.
Found in 2014, the Heartbleed bug was a essential vulnerability in OpenSSL, an open-source encryption protocol that, on the time, was liable for powering a lot of the safe communications programming throughout the net. Giant firms like Google, Fb, Netflix, and Yahoo used it, as did an unlimited assortment of different purposes and companies, from VPNs to on the spot messaging and electronic mail platforms. Naturally, the invention of the bug, which allowed an attacker to trick weak servers into handing over delicate information like usernames and passwords, commenced outright panic all through a lot of the web.
“We discovered {that a} factor that everyone used was being supported by only a couple individuals who weren’t actually being paid for it in any respect,” stated Jon Callas, a cryptography skilled and software program engineer, recalling the chaos that erupted on the time. Callas didn’t work on the OpenSSL crew, however he knew the individuals who did, and he labored on an analogous venture on the time.
As Callas alludes to, the issue with OpenSSL appeared to inevitably come again to the maintainers. Certainly, it might come out that OpenSSL, liable for securing privateness and safety companies for droves of main blue chip firms, was really maintained by a small, 11-person crew, the likes of which included a “core” crew of 4 individuals and just one full-time worker.
“It’s a actual drawback,” Callas stated, of the open supply’s upkeep points. Callas has some expertise with this, having been one of many key architects behind OpenPGP, an open customary of PGP encryption used extensively all through the web. “Determining how software program packages—that are principally [digital] infrastructure—get supported and maintained is a large challenge.”
Heartbleed uncovered an actual drawback with what had been the working paradigm for open-source safety till that point. For years, the FOSS world was guided by a doctrine that stated open-source software program was safer than industrial software program. The reasoning goes that FOSS’s transparency, with its code open to your complete net, allowed for higher visibility into its flaws—and thus, higher alternative to repair these flaws. That is what is called the “extra eyes” argument. So the pondering went, industrial software program solely had one improvement crew to look out for bugs; open supply had your complete web.
There’s a chic logic to this argument but it surely additionally has shortcomings. The “extra eyes” argument works in a perfect world—one the place FOSS tasks get every little thing they want. After all, in the true world, open supply is just as safe because the sources and folks allotted to sustaining it. As a rule, FOSS tasks have fewer eyes than they want, no more. Or, possibly they may have the incorrect eyes them—like these of a cybercriminal.
It’s plain that a certain quantity of FOSS tasks are extremely safe. The Linux kernel is stated to have been pored over by some 14,000 totally different contributors since 2005. The Linux Basis employs round 150 individuals and introduced in an estimated $262.6 million in revenues final yr, a majority of which got here from company and personal contributions. In some ways, it’s due to that help and transparency that onlookers have been capable of catch Jia Tan, the obvious progenitor of the XZ vulnerability. However the issue with utilizing Linux as an exemplar of open-source safety is fairly apparent: Most open-source tasks should not Linux and they don’t get Linux-level help.
The Backstabber’s Knife Assortment
When Heartbleed occurred, it was thought of a “wake-up name” for the software program group. The incident basically pivoted company America’s consideration to the safety points surrounding open supply for the primary time. It additionally compelled the Linux Basis to create the Core Infrastructure Initiative, which sought to establish open-source tasks of significant significance that wanted extra help (it was changed by the OSSF in October of 2021).
But if Heartbleed was a canary within the digital coal mine, it finally wasn’t one that everyone heeded. Certainly, the risk panorama since 2014 has solely gotten extra advanced, as FOSS has turn out to be a bigger and extra integral a part of the net. At the moment, the issues aren’t restricted to the occasional catastrophic bug. Certainly, they’re a complete lot extra sophisticated than that.
In our fashionable world, industrial software program is all over the place. Our lives are extra digital and interconnected than ever earlier than and just about every little thing you personal—out of your vacuum to your train tools to your toothbrush—comes with an app. In consequence, the chance for the software program working all of these apps to be compromised has expanded significantly. At the moment, so-called software program “provide chain assaults” are comparatively widespread. Such assaults take goal at notably weak software program parts, generally permitting cybercriminals to take advantage of one weak piece to take over or corrupt a complete product or system. As a rule, the parts that enable preliminary entry into provide chains are FOSS. There are such a lot of methods to hack open-source parts inside provide chains that the catalog of vulnerabilities was nicknamed the “backstabber’s knife assortment” in a single notable article from 2020.
One one who is aware of this advanced risk panorama effectively is Dan Lorenc. A seasoned safety skilled with a background in FOSS, Lorenc spent practically a decade working at Google, and at the least three years working cybersecurity element for Google Cloud. Lorenc now owns the availability chain safety enterprise Chainguard, which handles lots of the similar points that cropped up throughout his stint with Google.
“I feel open supply faces some distinctive challenges, largely simply due to the decentralized nature [of its development]. You may’t essentially belief all people writing the code,” stated Lorenc. “Anyone on the web can contribute to open supply code however not all people on the web is a pleasant individual.”
Sure, the unlucky reality is that the XZ episode is way from the primary time {that a} FOSS maintainer or contributor has launched malicious software program right into a venture. A 2020 report discovered that whereas most bugs in FOSS are merely coding errors, roughly 17 %—or a couple of fifth—have been maliciously launched bugs, or what researchers known as “bugdoors.” One infamous instance of this occurred in 2018, when the developer of a well-liked open-source program known as event-stream was bored with sustaining the venture and determined to cede management to a different developer—a pseudonymous net person named “Right9ctrl.” The one drawback was that “Right9ctrl” turned out to be a cybercriminal, who subsequently launched a malicious replace into the software program. The replace enabled the legal to hack right into a sure model of cryptocurrency wallets and steal their funds. The malicious code, downloaded some 8 million instances, went unnoticed for about two months.
The pattern of FOSS builders sabotaging their very own tasks has additionally been trending upward. In October of 2021, the maintainer of a well-liked set of npm libraries, a person named Marak Squires, inexplicably destroyed them with a collection of weird updates. The updates induced the software program to regurgitate a stream of incoherent gibberish that successfully ruined no matter venture was working the software program. It’s estimated that this act of digital self-immolation led to the destruction of “hundreds” of software program tasks that relied upon coding libraries for fulfillment.
Lorenc additionally says that there are undoubtedly extra “log4js” on the market—essential tasks that simply aren’t getting the eye or upkeep they deserve. Truly, this type of scenario pops up “on a regular basis,” he stated.
In instances the place such tasks blow up in company customers’ faces, the blame usually will get positioned on the maintainers. Individuals insinuate that “they’re not doing their jobs professionally, [or] not spending sufficient time on it,” Lorenc stated. “However, actually, it’s an advanced drawback. They [the maintainers] put one thing on the market without cost after which individuals will begin constructing a big piece of essential manufacturing infrastructure on prime of it and complain later when bugs are discovered.”
Taking Stock
So, what to do? How do you regulate a technological house that’s—by its very nature—deeply decentralized, suffering from anonymity, and structurally proof against any meddling by an overarching authority?
That query has been protecting lots of people up at evening. At varied instances for the reason that log4j debacle, I’ve reached out to executives at OpenSSF, Linux’s safety subsidiary, to debate progress on its “mobilization plan,” which, for those who’ll recall, was put collectively to create new safeguards for the FOSS setting after the log4shell bug was found. When initially proposed, the plan had a variety of transferring elements to it and it wasn’t precisely clear which of them would take precedence. In 2022, I spoke with the managing director of OpenSSF Brian Behlendorf, who informed me that there are at the least a few proposals inside the mobilization plan which can be primed for motion—ones he known as “shovel prepared.” One of the crucial promising options can be the obvious: forcing firms to stock the code they use.
Bizarre as it could sound, a variety of firms don’t try this. The OSSF has acknowledged that companies usually “haven’t any stock of the software program property they deploy, and infrequently haven’t any information concerning the parts inside the software program they’ve acquired.” Not tremendous interesting, proper? It’s a bit of like a building firm constructing a skyscraper however having no concept what the muse is fabricated from. Would you wish to stay or work in a constructing like that?

The mobilization plan known as for the widespread adoption of third-party code audits, recognized within the enterprise as a “software program invoice of supplies,” or SBOM. Such instruments present a list of a specific piece of software program, collected through algorithm. By telling a person what’s inside their very own program, SBOMs enable software program suppliers to test whether or not these particular person parts are affected by safety dangers or not.
“The easiest way to think about it’s as an ingredient checklist on the aspect of a bundle of meals,” stated Tim Mackey, who works with safety agency Synopsys, certainly one of a number of firms that provide SBOM companies. “The software program invoice of supplies is all about telling you what’s in there and the place it got here from.”
SBOMs have been round for years, however they’ve largely been used to weed out authorized dangers. As a result of FOSS utilization is girded upon a convoluted number of licensing agreements, firms have usually used SBOMs to find out a codebase’s contents and, due to this fact, what authorized agreements have to be abided by to keep away from getting sued. Now, nonetheless, they’re seeing adoption to mitigate a completely totally different form of threat.
In Could of 2021, the Biden administration issued an government order that, amongst different issues, mandated that each one software program contractors that work with the federal authorities use SBOMs. Mackey stated that, for the reason that order went by way of, his business has seen an explosion of curiosity. “It’s been an unimaginable enhance in enterprise,” he stated. “Improbable development.”
However even when SBOMs are a step in the fitting route, they aren’t finally a structural resolution to the bigger safety points posed by FOSS. Actually, they don’t do something to mitigate dangers that exist in code. “Actually, they’re simply type of correct asset stock,” stated former Google dev Dan Lorenc, noting that it’s “loopy” {that a} majority of firms don’t have already got that. “They [SBOMs] don’t repair the bugs, they don’t forestall bugs, they don’t cease attackers from tampering with stuff. They only offer you a great baseline.”
Cory Doctorow, a longtime member of the open-source group, says there are presently no incentives for firms to construct safe software program. When provide chain assaults occur, open-source maintainers get blamed, however the firms utilizing the code are actually those at fault. “We’re on this zone the place, not solely do firms not have any affirmative obligation to make it possible for their software program is sweet and that their maintainers really feel supported, however volunteers who line as much as warn” these firms and their prospects “about defects” will be “silenced by an organization in the event that they really feel that you just’re damaging their public picture.” Certainly, Doctorow says that it isn’t unusual for tech firms to sue safety researchers who attempt to reveal bugs of their merchandise.
The overall lack of motion by firms leaves a lot of the exhausting work of software program safety as much as particular person maintainers and open-source organizations just like the Linux Basis. To their credit score, these organizations have been working exhausting to provide you with new options to the safety points posed by FOSS. Along with encouraging SBOM adoption, the OpenSSF has pursued quite a few different safety initiatives over the previous a number of years. These applications embrace creating free safety purposes, like GUAC—a free software-tracking mechanism that permits coders to hunt for problematic parts of their code—and Sigstore, a cryptographic signature for verifying the validity of a developer’s software program.
If these efforts sound promising, it’s essential to notice that they’re happening in opposition to the backdrop of rising provide chain assaults, ongoing maintainer burnout, and a basic feeling that the safety posture of the open supply setting has not modified a lot for the reason that days of log4j. Some have argued that nothing wanting a system-wide overhaul will safe the Web. Matthew Hodgson, the co-founder of the encrypted protocol Matrix, just lately argued that FOSS ought to be a publicly funded service, one which—very like America’s actual, bodily infrastructure—receives ongoing federal funding and help.
After all, the probability that such a drastic transformation will really occur appears marginal, which leaves those that preserve the open-source ecosystem with a Sisyphean activity. Since final summer time, Brian Behlendorf has moved on to a different place inside the Linux Basis, passing the safety torch to former Google Cloud engineer Omkhar Arasaratnam, who now serves as basic supervisor of OpenSSF. Arasaratnam describes his job as “securing the web,” a activity he admits is “extremely troublesome.” A greater descriptor could be “unimaginable.” Nonetheless, he admits that whereas there are not any silver bullets, he can’t assist however be hopeful due to what’s at stake. “If we get this proper, we assist 8 billion individuals,” he says.








![It is iPadmania! [The CultCast] | Cult of Mac It is iPadmania! [The CultCast] | Cult of Mac](https://i1.wp.com/www.cultofmac.com/wp-content/uploads/2024/05/2024-iPad-Pro-and-iPad-Air-The-CultCast-episode-646.jpg?w=440&resize=440,0&ssl=1)
![It is iPadmania! [The CultCast] | Cult of Mac It is iPadmania! [The CultCast] | Cult of Mac](https://i1.wp.com/www.cultofmac.com/wp-content/uploads/2024/05/2024-iPad-Pro-and-iPad-Air-The-CultCast-episode-646.jpg?w=320&resize=320,0&ssl=1)


Leave a Comment